Download Decryption Text - Code Breaking Software Free
DownloadDecryptionTextCodeBreakingSoftwarefree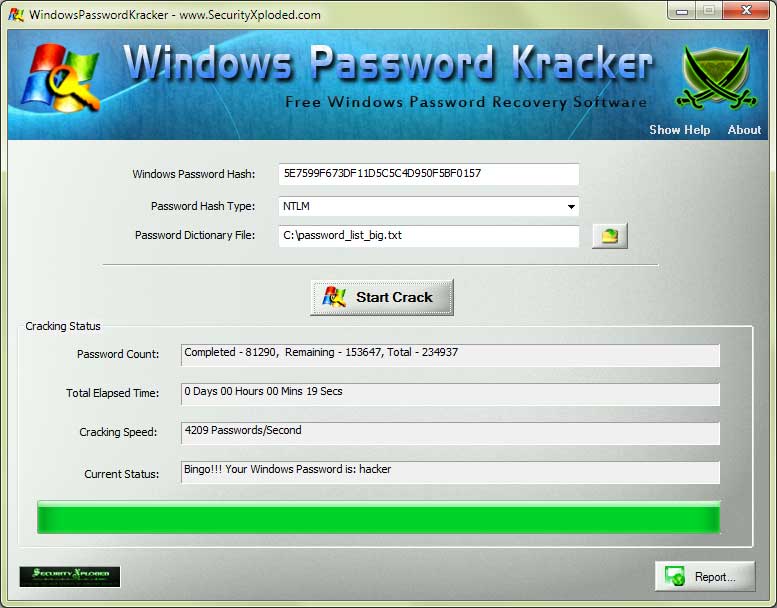
 ApexSQL Refactor is a free SQL formatter and code refactoring addin for SSMS and VS. Format SQL queries, refactor TSQL code, database tables and more. Cryptography WikipediaSecret code redirects here. For the Aya Kamiki album, see Secret Code. Cryptography or cryptology from Greekkrypts, hidden, secret and graphein, writing, or logia, study, respectively1 is the practice and study of techniques for secure communication in the presence of third parties called adversaries. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages 3 various aspects in information security such as data confidentiality, data integrity, authentication, and non repudiation4 are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip based payment cards, digital currencies, computer passwords, and military communications. Download the free trial version below to get started. Doubleclick the downloaded file to install the software. This paper, written in 2001, once one of the first public documents that discussed tools and techniques useful for understanding inner workings of malware such as. Until modern times, cryptography referred almost exclusively to encryption, which is the process of converting ordinary information called plaintext into. This definition explains the meaning of encryption and the importance of using encryption to protect data from being accessed by unauthorized users. SafeNet data encryption and crypto management solutions secure data in databases, applications, storage systems, virtualized platforms, and the cloud. Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. The cryptography literature often uses the name Alice A for the sender, Bob B for the intended recipient, and Eve eavesdropper for the adversary. Since the development of rotor cipher machines in World War I and the advent of computers in World War II, the methods used to carry out cryptology have become increasingly complex and its application more widespread. Modern cryptography is heavily based on mathematical theory and computer science practice cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure theoretical advances, e. There exist information theoretically secure schemes that provably cannot be broken even with unlimited computing poweran example is the one time padbut these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms. The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptographys potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and copyright infringement of digital media. Terminologyedit. Alphabet shift ciphers are believed to have been used by Julius Caesar over 2,0. This is an example with k3. In other words, the letters in the alphabet are shifted three in one direction to encrypt and three in the other direction to decrypt. Download Decryption Text - Code Breaking Software Free' title='Download Decryption Text - Code Breaking Software Free' />Until modern times, cryptography referred almost exclusively to encryption, which is the process of converting ordinary information called plaintext into unintelligible text called ciphertext. Decryption is the reverse, in other words, moving from the unintelligible ciphertext back to plaintext. A cipher or cypher is a pair of algorithms that create the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and in each instance by a key. The key is a secret ideally known only to the communicants, usually a short string of characters, which is needed to decrypt the ciphertext. Formally, a cryptosystem is the ordered list of elements of finite possible plaintexts, finite possible cyphertexts, finite possible keys, and the encryption and decryption algorithms which correspond to each key. Keys are important both formally and in actual practice, as ciphers without variable keys can be trivially broken with only the knowledge of the cipher used and are therefore useless or even counter productive for most purposes. Historically, ciphers were often used directly for encryption or decryption without additional procedures such as authentication or integrity checks. There are two kinds of cryptosystems symmetric and asymmetric. Super Smash Flash 2 Swf there. In symmetric systems the same key the secret key is used to encrypt and decrypt a message. Data manipulation in symmetric systems is faster than asymmetric systems as they generally use shorter key lengths. Asymmetric systems use a public key to encrypt a message and a private key to decrypt it. Codes. Caesar Cipher This is an online, JavaScript enabled version of a Caesar cipher program, for you to try. Also, there is a FREE version of the Caesar cipher. Electronic Frontier Foundation, the Creative Commons, and the Tor Project. Screenshots. Main dashboard screenshots are from UpdraftPlus Premium, so may reference some features that are not part of the free version. Configuring your backups. Background. Hexadecimal is a base16 numeral system used in the fields of computer programming and mathematics. The key is an ordinary number most widely known by its. Use of asymmetric systems enhances the security of communication. Examples of asymmetric systems include RSA Rivest Shamir Adleman, and ECC Elliptic Curve Cryptography. Symmetric models include the commonly used AES Advanced Encryption Standard which replaced the older DES Data Encryption Standard. In colloquial use, the term code is often used to mean any method of encryption or concealment of meaning. However, in cryptography, code has a more specific meaning. It means the replacement of a unit of plaintext i. Cryptanalysis is the term used for the study of methods for obtaining the meaning of encrypted information without access to the key normally required to do so i. Some use the terms cryptography and cryptology interchangeably in English, while others including US military practice generally use cryptography to refer specifically to the use and practice of cryptographic techniques and cryptology to refer to the combined study of cryptography and cryptanalysis. English is more flexible than several other languages in which cryptology done by cryptologists is always used in the second sense above. RFC 2. 82. 8 advises that steganography is sometimes included in cryptology. The study of characteristics of languages that have some application in cryptography or cryptology e. History of cryptography and cryptanalysiseditBefore the modern era, cryptography focused on message confidentiality i. Encryption attempted to ensure secrecy in communications, such as those of spies, military leaders, and diplomats. In recent decades, the field has expanded beyond confidentiality concerns to include techniques for message integrity checking, senderreceiver identity authentication, digital signatures, interactive proofs and secure computation, among others. Classic cryptographyeditThe main classical cipher types are transposition ciphers, which rearrange the order of letters in a message e. Latin alphabet. Simple versions of either have never offered much confidentiality from enterprising opponents. An early substitution cipher was the Caesar cipher, in which each letter in the plaintext was replaced by a letter some fixed number of positions further down the alphabet. Suetonius reports that Julius Caesar used it with a shift of three to communicate with his generals. Atbash is an example of an early Hebrew cipher. Download Decryption Text - Code Breaking Software Free' title='Download Decryption Text - Code Breaking Software Free' />The earliest known use of cryptography is some carved ciphertext on stone in Egypt ca 1. BCE, but this may have been done for the amusement of literate observers rather than as a way of concealing information. AACS encryption key controversy Wikipedia. This article needs to be updated. Please update this article to reflect recent events or newly available information. April 2. Internet users began circulating versions of this image, calling it the Free Speech Flag, in blog posts on dozens of websites and as user avatars on forums such as Digg. The first fifteen bytes of the 0. F9 key are contained in the RGB encoding of the five colors, with each color providing three bytes of the key. The byte C0 is appended in the lower right corner. A controversy surrounding the AACS cryptographic key arose in April 2. Motion Picture Association of America and the Advanced Access Content System Licensing Administrator, LLC AACS LA began issuing cease and desist letters7 to websites publishing a 1. F9 1. 1 0. 2 9. D 7. E3 5. B D8 4. 1 5. C5 6. 3 5. 6 8. 8 C089 commonly referred to as 0. F9,1. 01. 1 a cryptographickey for HD DVDs and Blu ray Discs. The letters demanded the immediate removal of the key and any links to it, citing the anti circumvention provisions of the United States Digital Millennium Copyright Act DMCA. In response to widespread Internet postings of the key, the AACS LA issued various press statements, praising those websites that complied with their requests as acting in a responsible manner, warning that legal and technical tools were adapting to the situation. The controversy was further escalated in early May 2. Digg received a DMCA cease and desist notice and then removed numerous articles on the matter and banned users reposting the information. This sparked what some describe as a digital revolt1. Digg, and throughout the Internet en masse, thereby leading to a Streisand effect. The AACS LA described this situation as an interesting new twist. BackgroundeditHexadecimal is a base 1. The key is an ordinary number most widely known by its hexadecimal representation in decimal notation, it is 1. Because the encryption key may be used as part of circumvention technology forbidden by the DMCA, its possession and distribution has been viewed as illegal by the AACS, as well as by some legal professionals. Since it is a 1. 28 bitnumerical value, it was dubbed an illegal number. Opponents to the expansion of the scope of copyright criticize the idea of making a particular number illegal. Commercial HD DVDs and Blu ray Discs integrate copy protection technology specified by the AACS LA. There are several interlocking encryption mechanisms, such that cracking one part of the system does not necessarily crack other parts. Therefore, the 0. F9 key is only one of many parts that are needed to play a disc on an unlicensed player. AACS can be used to revoke a key of a specific playback device, after it is known to have been compromised, as it has for Win. DVD. 2. 2 The compromised players can still be used to view old discs, but not newer releases without encryption keys for the compromised players. If other players are then cracked, further revocation would lead to legitimate users of compromised players being forced to upgrade or replace their player software or firmware in order to view new discs. Each playback device comes with a binary tree of secret device and processing keys. The processing key in this tree, a requirement to play the AACS encrypted discs, is selected based on the device key and the information on the disc to be played. As such, a processing key such as the 0. F9 key is not revoked, but newly produced discs cause the playback devices to select a different valid processing key to decrypt the discs. Timeline of AACS crackingeditOn December 2. Backup. HDDVD and its source code on the DVD decryption forum at the website Doom. Backup. HDDVD can be used to decrypt AACS protected content once one knows the encryption key. HD DVDs using a software player, and that finding them is not difficult. On January 1, 2. 00. On January 1. 2, 2. RAM while running Win. DVD. On or about January 1. Google search engine. By converting these results to hexadecimal, a correct key could be formed. Later that day, the first cracked HD DVD, Serenity, was uploaded on a private torrent tracker. The AACS LA confirmed on January 2. HD DVDs had been published without authorization. Doom. 9. org forum user arnezami found and published the 0. F9 AACS processing key on February 1. Nothing was hacked, cracked or even reverse engineered btw I only had to watch the show in my own memory. No debugger was used, no binaries changed. This key is not specific to any playback device or DVD title. Doom. 9. org forum user jx. March 4 to have revealed Cyber. Links Power. DVDs key, and that it was the key in use by Any. DVD. 3. 2The AACS LA announced on April 1. DVD players, which will not be able to decrypt AACS encrypted disks mastered after April 2. On May 1. 7, one week before any discs with the updated processing key had reached retail, claims were reported of the new keys having been retrieved from a preview disc of The Matrix Trilogy. On May 2. 3, the key 4. F E1 0. 4 2. 2 CA 2. C4 9. 3 3. F 9. 5 0. B 7. 9 2. A B2 was posted on Edward Feltens Freedom to Tinker Blog3. Doom. 9 as the new processing key MKB v. In August, two new processing keys were posted 3. F1 9. 0 A1 E8 1. 7 8. D 8. 0 6. 4 3. 4 9. F 8. 0 3. 1 D9 C8, for MKB v. A 5. F 8. A 0. 9 F8 3. F7 2. 2 1. B D4 1. F A6 4. C 9. C 7. MKB v. 6, MKB v. 7 and MKB v. In March, two additional processing keys were posted 3. C8 7. 2 9. 4 CE 8. F9 CC EB 5. 9 8. 4 B5 4. EE C1 8. D 6. 6, for MKB v. F 6. E 4. 0 3. C DF 1. E 4. 1 DF AA 2. 5 7. D 3. 1 3. F, for MKB v. In April, MKBv. 12 and MKBv. BB 1. 8 0. E 8. 3 2. EE 5. 9 6. C EF 6. B2, for MKB v. 12 and MKB v. In September, more processing keys were posted. EB DA DF 8. 8 DC C9 3. CB BE DB 9. E E0 9. F6, for MKB v. 141. F A8 BE 8. 2 8. 5 0. D 0. 5 D2 FC CE FF 3. D2, for MKB v. 17. AD 5. E 5. 4 6. C 4. D7 2. D C0 8. 3 AE B5 6. E1 B3, for MKB v. FC E7 8. E CD 3. 5 2. D A5 0. D 5. 2 6. B 5. E E3 D3 D9 6. B, for MKB v. 202. C3 2. 2 3. 8 9. 7 6. F F4 4. A 5. 1 E2 D3 3. CF E8 5. 7 7. 2, for MKB v. DMCA notices and Diggedit. Screenshot of the Digg front page during the user revolt all stories are related to the HD DVD key. As early as April 1. AACS LA had issued DMCA violation notices, sent by Charles S. Sims of Proskauer Rose. Following this, dozens of notices were sent to various websites hosted in the United States. On May 1, 2. 00. 7, in response to a DMCA demand letter, technology news site Digg began closing accounts and removing posts containing or alluding to the key. The Digg community reacted by creating a flood of posts containing the key, many using creative ways of semi directly or indirectly inserting the number, such as in song or images either representing the digits pictorially or directly representing bytes from the key as colors or on merchandise. At one point, Diggs entire homepage was covered with links to the HD DVD code or anti Digg references. Eventually the Digg administrators reversed their position, with founder Kevin Rose stating But now, after seeing hundreds of stories and reading thousands of comments, youve made it clear. Youd rather see Digg go down fighting than bow down to a bigger company. We hear you, and effective immediately we wont delete stories or comments containing the code and will deal with whatever the consequences might be.
ApexSQL Refactor is a free SQL formatter and code refactoring addin for SSMS and VS. Format SQL queries, refactor TSQL code, database tables and more. Cryptography WikipediaSecret code redirects here. For the Aya Kamiki album, see Secret Code. Cryptography or cryptology from Greekkrypts, hidden, secret and graphein, writing, or logia, study, respectively1 is the practice and study of techniques for secure communication in the presence of third parties called adversaries. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages 3 various aspects in information security such as data confidentiality, data integrity, authentication, and non repudiation4 are central to modern cryptography. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, electrical engineering, communication science, and physics. Applications of cryptography include electronic commerce, chip based payment cards, digital currencies, computer passwords, and military communications. Download the free trial version below to get started. Doubleclick the downloaded file to install the software. This paper, written in 2001, once one of the first public documents that discussed tools and techniques useful for understanding inner workings of malware such as. Until modern times, cryptography referred almost exclusively to encryption, which is the process of converting ordinary information called plaintext into. This definition explains the meaning of encryption and the importance of using encryption to protect data from being accessed by unauthorized users. SafeNet data encryption and crypto management solutions secure data in databases, applications, storage systems, virtualized platforms, and the cloud. Cryptography prior to the modern age was effectively synonymous with encryption, the conversion of information from a readable state to apparent nonsense. The originator of an encrypted message shared the decoding technique needed to recover the original information only with intended recipients, thereby precluding unwanted persons from doing the same. The cryptography literature often uses the name Alice A for the sender, Bob B for the intended recipient, and Eve eavesdropper for the adversary. Since the development of rotor cipher machines in World War I and the advent of computers in World War II, the methods used to carry out cryptology have become increasingly complex and its application more widespread. Modern cryptography is heavily based on mathematical theory and computer science practice cryptographic algorithms are designed around computational hardness assumptions, making such algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but it is infeasible to do so by any known practical means. These schemes are therefore termed computationally secure theoretical advances, e. There exist information theoretically secure schemes that provably cannot be broken even with unlimited computing poweran example is the one time padbut these schemes are more difficult to implement than the best theoretically breakable but computationally secure mechanisms. The growth of cryptographic technology has raised a number of legal issues in the information age. Cryptographys potential for use as a tool for espionage and sedition has led many governments to classify it as a weapon and to limit or even prohibit its use and export. In some jurisdictions where the use of cryptography is legal, laws permit investigators to compel the disclosure of encryption keys for documents relevant to an investigation. Cryptography also plays a major role in digital rights management and copyright infringement of digital media. Terminologyedit. Alphabet shift ciphers are believed to have been used by Julius Caesar over 2,0. This is an example with k3. In other words, the letters in the alphabet are shifted three in one direction to encrypt and three in the other direction to decrypt. Download Decryption Text - Code Breaking Software Free' title='Download Decryption Text - Code Breaking Software Free' />Until modern times, cryptography referred almost exclusively to encryption, which is the process of converting ordinary information called plaintext into unintelligible text called ciphertext. Decryption is the reverse, in other words, moving from the unintelligible ciphertext back to plaintext. A cipher or cypher is a pair of algorithms that create the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and in each instance by a key. The key is a secret ideally known only to the communicants, usually a short string of characters, which is needed to decrypt the ciphertext. Formally, a cryptosystem is the ordered list of elements of finite possible plaintexts, finite possible cyphertexts, finite possible keys, and the encryption and decryption algorithms which correspond to each key. Keys are important both formally and in actual practice, as ciphers without variable keys can be trivially broken with only the knowledge of the cipher used and are therefore useless or even counter productive for most purposes. Historically, ciphers were often used directly for encryption or decryption without additional procedures such as authentication or integrity checks. There are two kinds of cryptosystems symmetric and asymmetric. Super Smash Flash 2 Swf there. In symmetric systems the same key the secret key is used to encrypt and decrypt a message. Data manipulation in symmetric systems is faster than asymmetric systems as they generally use shorter key lengths. Asymmetric systems use a public key to encrypt a message and a private key to decrypt it. Codes. Caesar Cipher This is an online, JavaScript enabled version of a Caesar cipher program, for you to try. Also, there is a FREE version of the Caesar cipher. Electronic Frontier Foundation, the Creative Commons, and the Tor Project. Screenshots. Main dashboard screenshots are from UpdraftPlus Premium, so may reference some features that are not part of the free version. Configuring your backups. Background. Hexadecimal is a base16 numeral system used in the fields of computer programming and mathematics. The key is an ordinary number most widely known by its. Use of asymmetric systems enhances the security of communication. Examples of asymmetric systems include RSA Rivest Shamir Adleman, and ECC Elliptic Curve Cryptography. Symmetric models include the commonly used AES Advanced Encryption Standard which replaced the older DES Data Encryption Standard. In colloquial use, the term code is often used to mean any method of encryption or concealment of meaning. However, in cryptography, code has a more specific meaning. It means the replacement of a unit of plaintext i. Cryptanalysis is the term used for the study of methods for obtaining the meaning of encrypted information without access to the key normally required to do so i. Some use the terms cryptography and cryptology interchangeably in English, while others including US military practice generally use cryptography to refer specifically to the use and practice of cryptographic techniques and cryptology to refer to the combined study of cryptography and cryptanalysis. English is more flexible than several other languages in which cryptology done by cryptologists is always used in the second sense above. RFC 2. 82. 8 advises that steganography is sometimes included in cryptology. The study of characteristics of languages that have some application in cryptography or cryptology e. History of cryptography and cryptanalysiseditBefore the modern era, cryptography focused on message confidentiality i. Encryption attempted to ensure secrecy in communications, such as those of spies, military leaders, and diplomats. In recent decades, the field has expanded beyond confidentiality concerns to include techniques for message integrity checking, senderreceiver identity authentication, digital signatures, interactive proofs and secure computation, among others. Classic cryptographyeditThe main classical cipher types are transposition ciphers, which rearrange the order of letters in a message e. Latin alphabet. Simple versions of either have never offered much confidentiality from enterprising opponents. An early substitution cipher was the Caesar cipher, in which each letter in the plaintext was replaced by a letter some fixed number of positions further down the alphabet. Suetonius reports that Julius Caesar used it with a shift of three to communicate with his generals. Atbash is an example of an early Hebrew cipher. Download Decryption Text - Code Breaking Software Free' title='Download Decryption Text - Code Breaking Software Free' />The earliest known use of cryptography is some carved ciphertext on stone in Egypt ca 1. BCE, but this may have been done for the amusement of literate observers rather than as a way of concealing information. AACS encryption key controversy Wikipedia. This article needs to be updated. Please update this article to reflect recent events or newly available information. April 2. Internet users began circulating versions of this image, calling it the Free Speech Flag, in blog posts on dozens of websites and as user avatars on forums such as Digg. The first fifteen bytes of the 0. F9 key are contained in the RGB encoding of the five colors, with each color providing three bytes of the key. The byte C0 is appended in the lower right corner. A controversy surrounding the AACS cryptographic key arose in April 2. Motion Picture Association of America and the Advanced Access Content System Licensing Administrator, LLC AACS LA began issuing cease and desist letters7 to websites publishing a 1. F9 1. 1 0. 2 9. D 7. E3 5. B D8 4. 1 5. C5 6. 3 5. 6 8. 8 C089 commonly referred to as 0. F9,1. 01. 1 a cryptographickey for HD DVDs and Blu ray Discs. The letters demanded the immediate removal of the key and any links to it, citing the anti circumvention provisions of the United States Digital Millennium Copyright Act DMCA. In response to widespread Internet postings of the key, the AACS LA issued various press statements, praising those websites that complied with their requests as acting in a responsible manner, warning that legal and technical tools were adapting to the situation. The controversy was further escalated in early May 2. Digg received a DMCA cease and desist notice and then removed numerous articles on the matter and banned users reposting the information. This sparked what some describe as a digital revolt1. Digg, and throughout the Internet en masse, thereby leading to a Streisand effect. The AACS LA described this situation as an interesting new twist. BackgroundeditHexadecimal is a base 1. The key is an ordinary number most widely known by its hexadecimal representation in decimal notation, it is 1. Because the encryption key may be used as part of circumvention technology forbidden by the DMCA, its possession and distribution has been viewed as illegal by the AACS, as well as by some legal professionals. Since it is a 1. 28 bitnumerical value, it was dubbed an illegal number. Opponents to the expansion of the scope of copyright criticize the idea of making a particular number illegal. Commercial HD DVDs and Blu ray Discs integrate copy protection technology specified by the AACS LA. There are several interlocking encryption mechanisms, such that cracking one part of the system does not necessarily crack other parts. Therefore, the 0. F9 key is only one of many parts that are needed to play a disc on an unlicensed player. AACS can be used to revoke a key of a specific playback device, after it is known to have been compromised, as it has for Win. DVD. 2. 2 The compromised players can still be used to view old discs, but not newer releases without encryption keys for the compromised players. If other players are then cracked, further revocation would lead to legitimate users of compromised players being forced to upgrade or replace their player software or firmware in order to view new discs. Each playback device comes with a binary tree of secret device and processing keys. The processing key in this tree, a requirement to play the AACS encrypted discs, is selected based on the device key and the information on the disc to be played. As such, a processing key such as the 0. F9 key is not revoked, but newly produced discs cause the playback devices to select a different valid processing key to decrypt the discs. Timeline of AACS crackingeditOn December 2. Backup. HDDVD and its source code on the DVD decryption forum at the website Doom. Backup. HDDVD can be used to decrypt AACS protected content once one knows the encryption key. HD DVDs using a software player, and that finding them is not difficult. On January 1, 2. 00. On January 1. 2, 2. RAM while running Win. DVD. On or about January 1. Google search engine. By converting these results to hexadecimal, a correct key could be formed. Later that day, the first cracked HD DVD, Serenity, was uploaded on a private torrent tracker. The AACS LA confirmed on January 2. HD DVDs had been published without authorization. Doom. 9. org forum user arnezami found and published the 0. F9 AACS processing key on February 1. Nothing was hacked, cracked or even reverse engineered btw I only had to watch the show in my own memory. No debugger was used, no binaries changed. This key is not specific to any playback device or DVD title. Doom. 9. org forum user jx. March 4 to have revealed Cyber. Links Power. DVDs key, and that it was the key in use by Any. DVD. 3. 2The AACS LA announced on April 1. DVD players, which will not be able to decrypt AACS encrypted disks mastered after April 2. On May 1. 7, one week before any discs with the updated processing key had reached retail, claims were reported of the new keys having been retrieved from a preview disc of The Matrix Trilogy. On May 2. 3, the key 4. F E1 0. 4 2. 2 CA 2. C4 9. 3 3. F 9. 5 0. B 7. 9 2. A B2 was posted on Edward Feltens Freedom to Tinker Blog3. Doom. 9 as the new processing key MKB v. In August, two new processing keys were posted 3. F1 9. 0 A1 E8 1. 7 8. D 8. 0 6. 4 3. 4 9. F 8. 0 3. 1 D9 C8, for MKB v. A 5. F 8. A 0. 9 F8 3. F7 2. 2 1. B D4 1. F A6 4. C 9. C 7. MKB v. 6, MKB v. 7 and MKB v. In March, two additional processing keys were posted 3. C8 7. 2 9. 4 CE 8. F9 CC EB 5. 9 8. 4 B5 4. EE C1 8. D 6. 6, for MKB v. F 6. E 4. 0 3. C DF 1. E 4. 1 DF AA 2. 5 7. D 3. 1 3. F, for MKB v. In April, MKBv. 12 and MKBv. BB 1. 8 0. E 8. 3 2. EE 5. 9 6. C EF 6. B2, for MKB v. 12 and MKB v. In September, more processing keys were posted. EB DA DF 8. 8 DC C9 3. CB BE DB 9. E E0 9. F6, for MKB v. 141. F A8 BE 8. 2 8. 5 0. D 0. 5 D2 FC CE FF 3. D2, for MKB v. 17. AD 5. E 5. 4 6. C 4. D7 2. D C0 8. 3 AE B5 6. E1 B3, for MKB v. FC E7 8. E CD 3. 5 2. D A5 0. D 5. 2 6. B 5. E E3 D3 D9 6. B, for MKB v. 202. C3 2. 2 3. 8 9. 7 6. F F4 4. A 5. 1 E2 D3 3. CF E8 5. 7 7. 2, for MKB v. DMCA notices and Diggedit. Screenshot of the Digg front page during the user revolt all stories are related to the HD DVD key. As early as April 1. AACS LA had issued DMCA violation notices, sent by Charles S. Sims of Proskauer Rose. Following this, dozens of notices were sent to various websites hosted in the United States. On May 1, 2. 00. 7, in response to a DMCA demand letter, technology news site Digg began closing accounts and removing posts containing or alluding to the key. The Digg community reacted by creating a flood of posts containing the key, many using creative ways of semi directly or indirectly inserting the number, such as in song or images either representing the digits pictorially or directly representing bytes from the key as colors or on merchandise. At one point, Diggs entire homepage was covered with links to the HD DVD code or anti Digg references. Eventually the Digg administrators reversed their position, with founder Kevin Rose stating But now, after seeing hundreds of stories and reading thousands of comments, youve made it clear. Youd rather see Digg go down fighting than bow down to a bigger company. We hear you, and effective immediately we wont delete stories or comments containing the code and will deal with whatever the consequences might be.